
Techniques

A Coding Guide to Implement Zarr for Large-Scale Data: Chunking, Compression, Indexing, and Visualization Techniques
In this tutorial, we take a deep dive into the capabilities of Zarr, a library designed for efficient storage & manipulation of large, multidimensional arrays. We begin by exploring the basics, creating arrays, setting chunking strategies, and modifying values directly on disk. From there, we expand into more advanced operations such as experimenting with chunk…

5 techniques I rely on to keep my Pixel phone juiced up for longer
Summary Keep tabs on battery metrics from within Settings to familiarize yourself with power and usage statistics. Proactive charging optimization and health assistance measures can ensure long-term battery life performance. Give the boot to non-essential apps running in the background to improve overall battery efficiency. There’s a lot to love about Google’s Pixel line of…
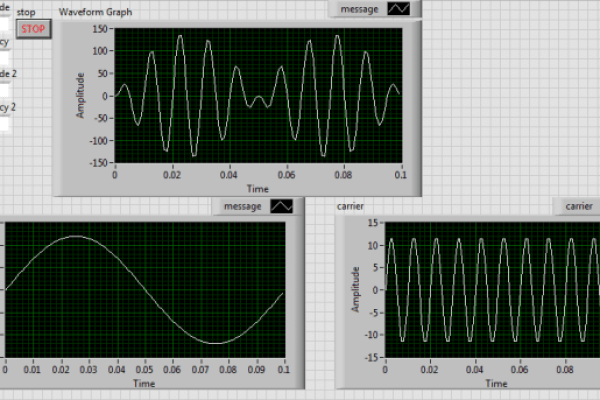
Exploring Analog And Digital Modulation Techniques Through Labview Simulation
– Advertisement – Communication systems form the backbone of modern technology, enabling the transfer of information across various platforms. At the heart of these systems lies modulation, a technique used to encode information onto carrier waves. Modulation is crucial for efficient signal transmission over long distances and across different mediums. There are two primary types…

Enhancing AI Inference: Advanced Techniques and Best Practices
When it comes to real-time AI-driven applications like self-driving cars or healthcare monitoring, even an extra second to process an input could have serious consequences. Real-time AI applications require reliable GPUs and processing power, which has been very expensive and cost-prohibitive for many applications – until now. By adopting an optimizing inference process, businesses can…

AI-Powered Social Engineering: Ancillary Tools and Techniques
Social engineering is advancing fast, at the speed of generative AI. This is offering bad actors multiple new tools and techniques for researching, scoping, and exploiting organizations. In a recent communication, the FBI pointed out: ‘As technology continues to evolve, so do cybercriminals’ tactics.’ This article explores some of the impacts of this GenAI-fueled acceleration….

Sliver Implant Targets German Entities With DLL Sideloading And Proxying Techniques – Cyble
Key Takeaways Cyble Research and Intelligence Labs (CRIL) has identified an ongoing cyberattack – targeting organizations in Germany. The attack is initiated through a deceptive LNK file embedded within an archive. When executed by an unsuspecting user, this LNK file triggers cmd.exe to copy and run wksprt.exe, a legitimate executable. This executable sideloads a malicious…



