The National Security Agency (NSA) is a federal government surveillance and intelligence agency that’s part of the U.S. Department of Defense and is managed under the authority of the director of national intelligence (DNI).
Led by the NSA director, the agency performs global electronic monitoring, collection and processing of information and data from its headquarters in Fort Meade, Md. It’s in the intelligence-gathering business and, unlike the Federal Bureau of Investigation (FBI), its agents don’t handle law enforcement and don’t make arrests. They also aren’t part of the U.S. military. The NSA does have a cooperative relationship with the FBI and the military, and shares intelligence with other government entities and the military.
Responsibilities of the NSA
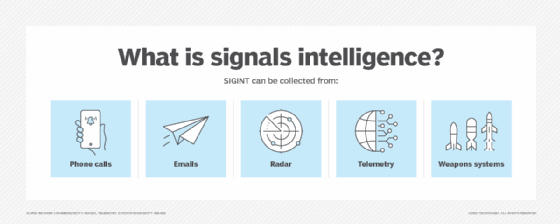
As a member of the intelligence community, the NSA exists to protect the integrity of U.S. national communications systems, and to collect and process signals intelligence. SIGINT is information that originates from foreign adversaries’ secret communications, typically digital and electronic systems, such as communications and radar systems. The NSA operates around the world in support of U.S. national security and foreign policy.
The NSA’s role in preserving national security is twofold:
- NSA analysts gather and decrypt intelligence from electronic communications found on a range of electronic sources, including phone calls, email, videos, photos, stored data and social networking.
- The agency uses discovered intelligence to protect the nation’s classified data and national security systems and guide policymakers in their decisions. These systems are crucial to intelligence, military operations and other government activities from unauthorized access and tampering by both domestic and foreign enemies.
In October 2017, U.S. Attorney General Loretta Lynch signed guidelines enabling the NSA to provide intercepted communications and raw SIGINT before applying domestic and foreign privacy protections to 16 government agencies, including the FBI and Central Intelligence Agency.
The number of NSA employees and its budget are classified information. However, the NSA employs analysts, engineers, physicists, linguists, computer science professionals, researchers, cybersecurity officers, data flow experts, managers, experts in intelligence analysis, customer relations and public affairs specialists, and administrative and clerical assistants.
It also claims to be the largest employer of mathematicians in the U.S. and possibly worldwide. NSA mathematicians and their counterparts in the Central Security Service (CSS), an NSA subagency, perform the agency’s two critical functions:
- They design cryptographic systems to protect U.S. communications and information assurance.
- They search for weaknesses in the counterpart systems of American adversaries.
The NSA has denied reports claiming it has an unlimited black budget that’s undisclosed even to other government agencies. Nevertheless, the agency has said that, if it were in the public sector, it would rank in the top 10% of Fortune 500 companies.
NSA programs
The NSA can listen in on every international phone call made to and from the U.S., but that’s just one aspect of the agency’s work. The agency’s bigger focus is on intelligence gathering.
For much of its history, it was thought that the NSA focused on gathering international intelligence. That changed in 2013 when details on other NSA surveillance programs became public.
That year, Edward Snowden, a Booz Allen Hamilton contractor at that time, leaked confidential NSA information to the national and international press. The documents indicated the agency had domestic surveillance activities that included the bulk collection of U.S. communications. Snowden told the press about 10 such surveillance programs:
- Prism. Perhaps the most infamous NSA program, Prism collected data stored by nine major Silicon Valley technology companies: AOL, Apple, Google, Meta (formerly Facebook), Microsoft, Paltalk, Skype, Yahoo and YouTube. The data collected included emails, file transfers, photos and voice calls.
- Fairview. Under this program, the NSA worked with AT&T to access massive amounts of international internet traffic passing through domestic U.S. networks. The NSA is reported to have partnered extensively with U.S. telecommunication operators for decades as part of this program.
- Blarney. This international version of the PRISM program was also said to be part of Fairview. Through Blarney, the NSA formed partnerships with foreign telecom operators to gain access to their customer data.
- Stormbrew and Oakstar. Like Blarney, these two programs fall under the Fairview umbrella. Stormbrew allegedly refers to a partnership with Verizon, according to a New York Times investigation. OAKSTAR has a number of subprograms that The Washington Post said are designed to collect “data as it moves across fiber-optic cables and the gateways that direct global communications traffic.”
- XKeyscore. According to The Guardian , a report on XKeyscore by the NSA listed the project as collecting “nearly everything a typical user does on the internet,” including the content of emails and chats, visible in real time.
- Marina, Trafficthief and Pinwale. Little is known about these three programs. However, as reported in The Daily Dot, Trafficthief is described as containing “metadata from a subset of tasked strong-selectors.” Pinwale contains “content selected from dictionary tasked terms,” while Marina stores “user activity metadata with front end full take feeds and backend selected feeds.”
- Boundless Informant. This is said to be a measure of how well the other programs are doing. Slides that Snowden gave The Guardian indicated that, in one month in 2012, the NSA collected almost 100 billion pieces of intelligence worldwide. Three billion pieces of intelligence were collected in the U.S. during that same period. Presumably, an email or phone call would constitute a piece of intelligence.
History of the NSA
Early information gathering and interception techniques relied on radio signals, radar and telemetry. In the U.S., the first traces of SIGINT date back to July 1917 when the government created the Cipher Bureau of Military Intelligence. This was three months after the United States had declared war on Germany, in part because of the infamous Zimmerman Telegram.
British intelligence intercepted and deciphered the Zimmerman Telegram. It revealed that the German foreign secretary had attempted to entice Mexico into war against the U.S. by promising to return the states of Texas, New Mexico and Arizona to Mexico should Germany win the war. The contents of the message inflamed the U.S. and proved the value of SIGINT.
After World War I, SIGINT and foreign signals intelligence work became fragmented and scattered among numerous government entities. The Army Signal Corps developed the Signal Intelligence Service (SIS) in 1929 after taking over cryptology from military intelligence. Civilian William F. Friedman became chief cryptologist at SIS and was tasked with teaching a team of civilians about cryptanalysis so they could compile codes for the U.S. Army.
The military’s success cracking German and Japanese codes during World War II, once again proved the merits of intelligence work. In 1952, President Truman officially established the National Security Agency with SIGINT operations under it. In 1957, the NSA moved to Fort Meade.
In 1972, a presidential directive established the Central Security Service to provide cryptologic support, knowledge and assistance to the military cryptologic community. The NSA and CSS together form the National Security Agency Central Security Service. The job of the NSA/CSS is to create a unified cryptologic effort with the armed forces. It’s also charged with working with senior military and civilian leaders to address and act on critical military-related issues in support of national and tactical intelligence objectives.
In 2012, The New York Times reported that the Stuxnet worm, discovered in June 2010 after a damaging attack on Windows machines and programmatic logic controllers in Iran’s industrial plants, including its nuclear program, had been jointly developed by the U.S. and Israel. Neither country has admitted responsibility for the attack.
In addition to protecting national security through cryptography and cryptanalysis, the NSA has weathered security breaches beyond Snowden that have embarrassed the agency and affected its intelligence-gathering capabilities.
In 2015, an unidentified NSA contractor removed classified government information, which included code and spyware used to infiltrate foreign computer network operations, from the agency and stored it on a personal device. Russian hackers allegedly intercepted the files. The contractor acknowledged using antivirus software from Kaspersky Lab.
In 2017, Israeli intelligence officers revealed that they detected NSA materials on Kaspersky networks in 2015. Kaspersky officials later admitted that they became aware of unusual files on an unidentified contractor’s computer, and they didn’t immediately report their findings. In December 2017, the U.S. government banned the use of Kaspersky Lab products for all federal agencies and government employees.
A hacker group calling itself The Shadow Brokers claimed it had stolen NSA files in 2017. It released batches of files on the internet, some of which allegedly contained the Internet Protocol addresses of computer servers that were compromised by the Equation Group, an organization reported to have ties to the NSA.
The continual dumping of NSA files has exposed zero-day exploits targeting firewalls and routers, Microsoft Windows vulnerabilities and other cyberweapons. The NSA, according to the ongoing leaks, has been stockpiling vulnerabilities, most notably the Windows EternalBlue exploit used by cybercriminals in the global WannaCry ransomware attacks.
The FBI arrested Harold T. Martin III, a former NSA contractor employed by Booz Allen Hamilton, in August 2016 and accused him of violating the Espionage Act for unlawful possession of terabytes of confidential materials allegedly taken from the NSA and other intelligence agencies over a 20-year period. A grand jury indicted him in February 2018. After pleading guilty to willful retention of national defense information, Martin was sentenced in 2019 to nine years in federal prison, followed by three years of supervised release.
In October 2020, the NSA released an advisory specifying 25 publicly known vulnerabilities actively exploited or being scanned by Chinese state-sponsored actors. Later that year, the NSA verified that SolarWinds Orion Platform version 2020.2.1 HF 2 eliminated the malicious code used in the extensive SolarWinds hack.
In January 2021, for the first time, the FBI, the Cybersecurity and Infrastructure Security Agency (CISA), the Office of the DNI and the NSA publicly suggested Russian threat actors were responsible for the SolarWinds supply chain attack.
That April, the Biden administration formally attributed the SolarWinds attacks to the Russian government’s Foreign Intelligence Service (SVR). The FBI, NSA and CISA jointly warned that state-sponsored, SVR-allied threats were actively exploiting known vulnerabilities to get access to national security and government-associated networks.
Among the NSA’s more recent developments is the 2020 launch of its Cybersecurity Collaboration Center. The CCC partners with public and private organizations to better detect and mitigate cybersecurity threats to their critical infrastructure. Its goals include hardening the U.S. Defense Industrial Base, preparing responses to foreign nation-state cyberthreats and developing mitigations for cybersecurity challenges.
In response to emerging artificial intelligence threats, in 2023 the NSA announced the creation of its AI Security Center to consolidate and centralize the agency’s AI activities.
Learn more about cybersecurity as a career path, what’s required and the various types of jobs these IT professionals do.









