Cybercriminals impersonate the trusted e-signature brand and send fake Docusign notifications to trick people into giving away their personal or corporate data
27 May 2025
•
,
5 min. read

Remember when you used to have to print, sign, scan, email and/or even fax every time you wanted to sign and send an official document? Today, much of the hard work is done behind the scenes by cloud app providers like Docusign.
But like all tech brands, once it has reached a critical mass of users, cybercriminals will look for ways to abuse it for their own ends. Docusign claims to have 1.6 million customers around the world, including 95% of the Fortune 500, and over one billion users. That has put it firmly in the crosshairs of threat actors. Read on to understand how to keep your employees safe from Docusign-themed phishing.
How does Docusign phishing work?
Social engineering is one of the biggest threats to your business. According to Verizon, phishing is now an initial access vector for 19% of data breaches, while a whopping 60% feature a “human element.” As a trusted and widely recognized brand, Docusign is a natural choice for threat actors looking to harvest corporate logins and potentially monetize attacks in other ways.
Victims will typically receive an email with a spoofed Docusign “envelope” requesting that they click on a large yellow box to “review document.” There may also be an attachment featuring a QR code. Both actions could lead to the same result: the victim is taken to a phishing site such as a fake Microsoft login page, and asked to enter personal and/or financial information.
QR codes are also popular as they require the user to scan with their mobile device, which may not have security software installed to prevent them from being taken to a malicious page. Either way, a targeted phishing attack like this could also enable threat actors to gain a crucial foothold in corporate networks, as well as for privilege escalation, lateral movement and data exfiltration/ransomware.
Some examples
Over the past few months, incidents have emerged of:
- “Legitimate” Docusign envelopes that spoof invoices from suppliers, in a bid to trick companies into transferring money.
- Fake invoice scams impersonating US state and municipal agencies and designed to trick suppliers into wiring money.
- Cybercriminals are not spoofing fake Docusign emails, but instead registering real accounts with the company, and using its APIs to send out legitimate envelopes spoofing popular brands.
- Regular phishing emails spoofing the Docusign brand and taking the user to phishing login pages. These could mimic corporate HR and payroll departments, or even external entities like municipal authorities.
- Refund scams which cite a fake transaction and try to force the victim into calling a number if they want to cancel it. Once on the phone, they’ll be persuaded to hand over their personal/financial/card details to claim the ‘refund’.
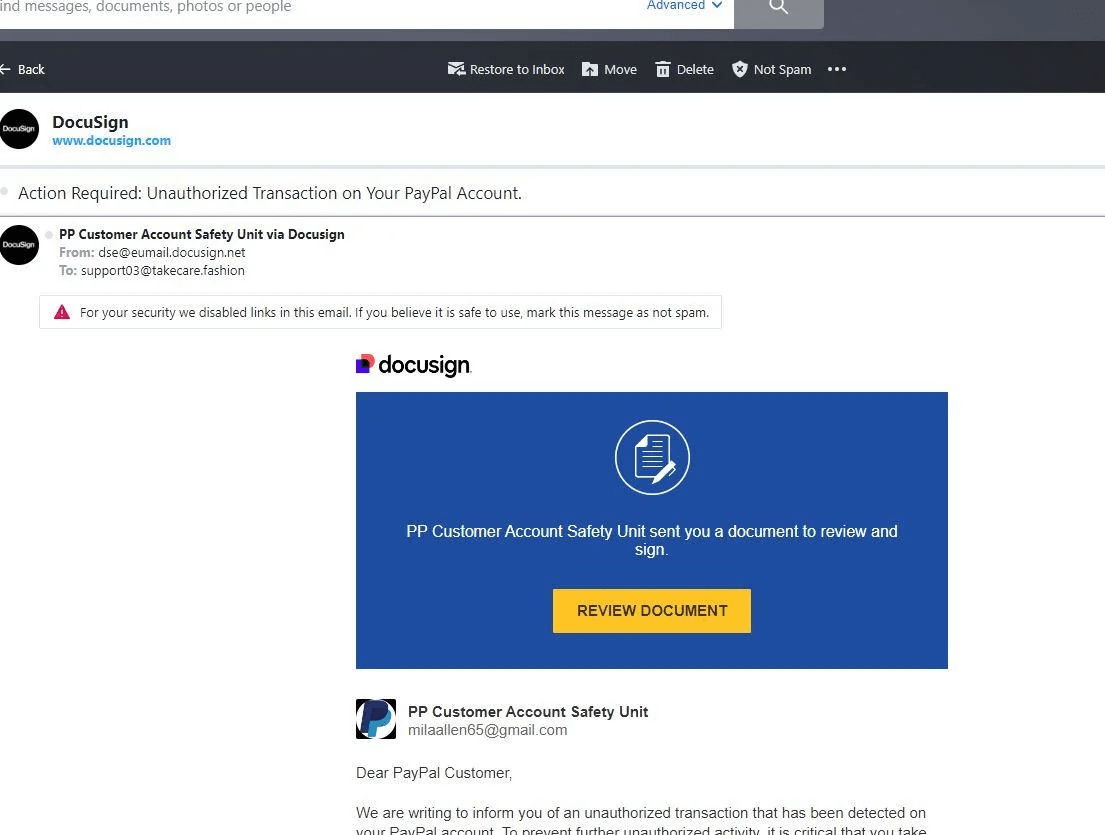
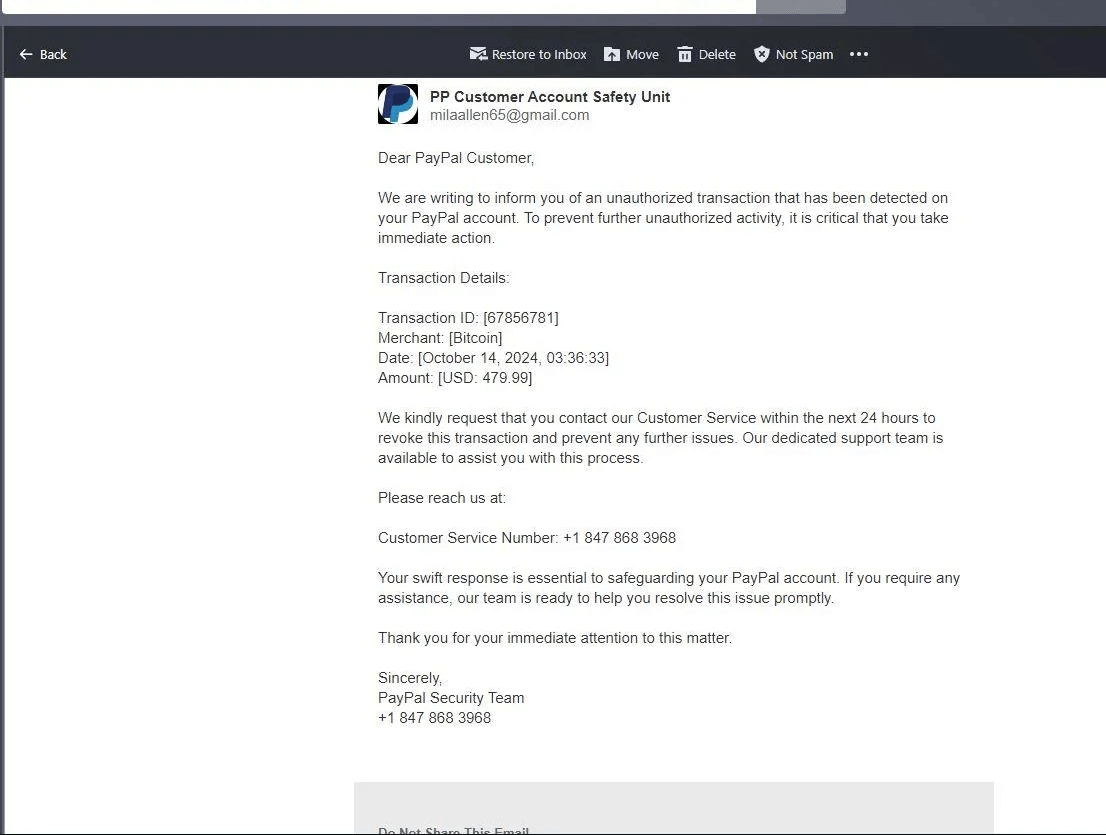
Example of a scam abusing people’s trust in Docusign for data theft (Source: Reddit)
Staying safe
Fortunately, there’s plenty you can do to keep yourself and your company safe from Docusign threats. From a company’s perspective, the first course of action is to be aware of the risks and update your phishing awareness programs to ensure staff are able to spot the warning signs of a scam email. Simulation tools should be customizable enough to support this.
Things workers should be taught to look out for include:
- Destination URLs: hover over any links/buttons in Docusign emails to check the destination URLs are legitimate.
- Security codes: these should feature on any legitimate Docusign email (in the “alternate sign in method” section) and allow the user to access a document directly on the Docusign site rather than follow links in an email.
- Attachments: there should be no attachments in an initial Docusign email. Only once a doc has been signed will you receive a finished version of it via attachment.
- Spelling, grammatical and tonal errors: are another tell-tale sign of a phishing email.
- An email signature and sender name/email address that don’t match.
Layer up defenses on top of the security awareness piece by including things like:
- Multi-factor authentication (MFA) for all corporate accounts, which will make it harder for hackers to access your data, even if they do manage to steal your logins.
- Password hygiene, including use of strong, unique passwords for each account, stored in a password manager.
- A multi-layered security tool from a reputable vendor like ESET, which, among other things, detects malicious attachments, prevents users from following links to phishing sites, and enables administrators to manually define email filtering conditions and actions.
- Updated policy to urge users not to open attachments or follow links in any unsolicited emails, and only access Docusign docs via the security code.
- Changing internal business processes regarding fund transfers, so that any large sums are subject to extra scrutiny.
- Encouraging users to report all suspicious Docusign-themed emails to your IT/security team and to spam@docusign.com.
What to do if you fall victim
If the worst happens and an employee does click through on a Docusign scam, you as an admin will need to work through a specific set of actions, including:
- Reset passwords for the impacted user, including any accounts that they may have reused credentials across
- Run a malware scan on the victim’s machine to detect and remove any malicious code
- Isolate the device from the network to contain the “blast radius” of an attack
- Monitor the dark web for signs of information theft/leakage
- Monitor the victim’s accounts for unusual activity
- Dig deeper with forensics to understand what the attacker wanted and whether they managed to gain elevated internal access
- Use the event as a learning moment for employees: encouraging them to report suspicious emails rapidly and to be on their guard in general about unsolicited emails
Of course, Docusign isn’t just used by businesses. You might have been exposed to it in a personal capacity when buying a house or completing tax paperwork. In that case, many of the tips above will still stand you in good stead. Electronic signing apps are a great time-saver. But make sure you don’t get caught out by scammers exploiting your trust in these apps.










